Capturing the Naughty app Traffic in Burpsuit
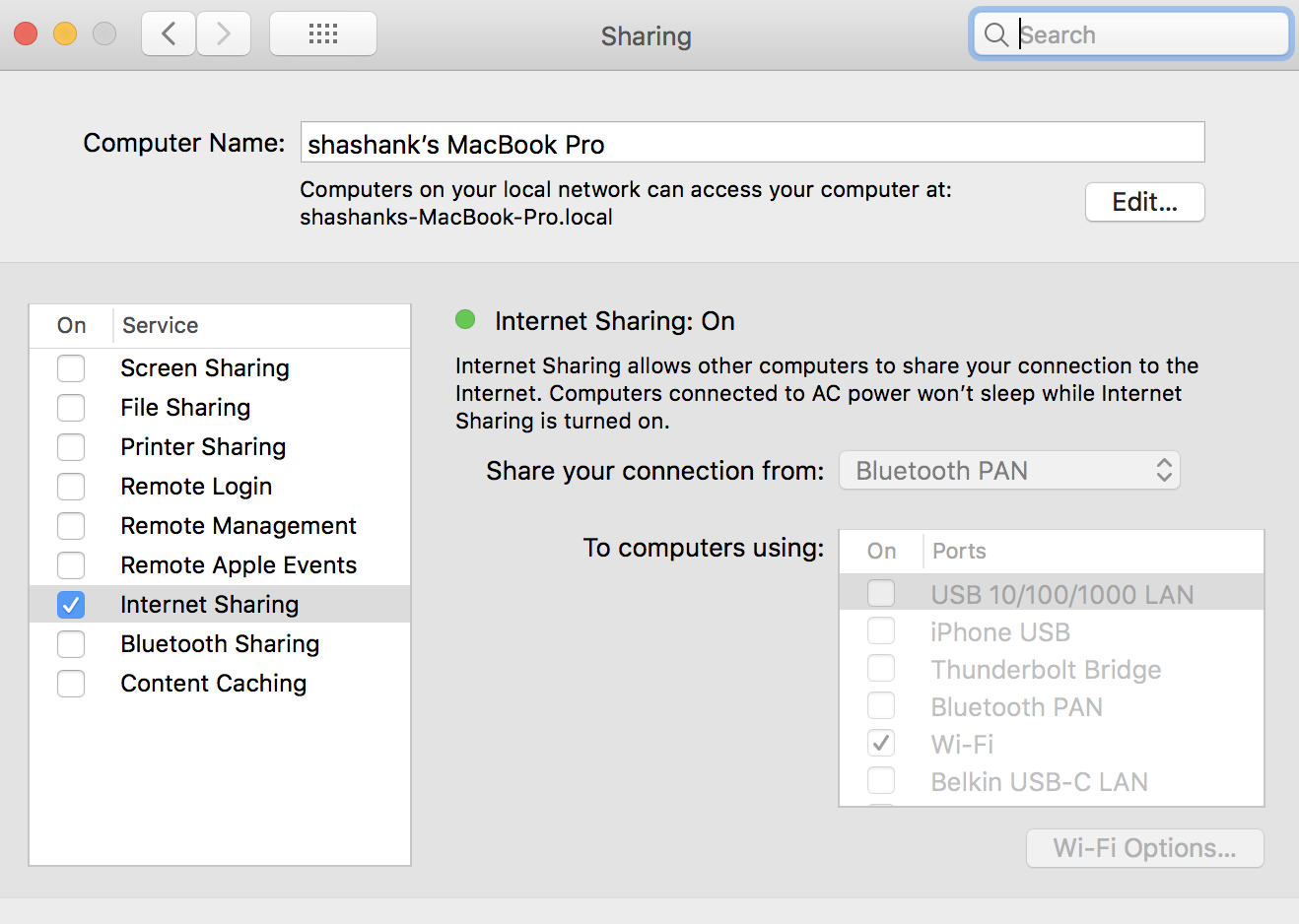
While performing the pen-testing of one of banking apps we came across challenge of capturing the traffic in the burp. App being naughty was bypassing burp proxy and we were not able to capture the requests/responses. Reversing the app we came to know it was built on Xamarain. To proceed with the pentest it was important to capture the requests in the burp proxy. Then we came across following link (Big thanks for this): https://gist.github.com/gameFace22/3afedd1309960249fa7fcb1360e40fd3 And it did work ! Just for my notes keeping the steps. Step 1: Switch off the wifi of the macbook and connect it to your phone hotspot. Connect it either by using cable to by bluetooth. Not by wifi ! Step 2: Go to System preferences-->Sharing-->On the internet sharing. See the pic. The internet which macbook gets from hotspot is shared by macbook. Macbook will start it's own hotspot ! Step 3: Now some command need to run to tell the macbook to route the traffic recei
